Transparent Data Encryption (TDE) is a CYBERTEC encryption patch for PostgreSQL and a part of PGEE.
The idea behind the patch is to store all the files which make up a PostgreSQL cluster securely on disk in an encrypted format (data-at-rest encryption). It then decrypts blocks as they are read from disk. However, the data remains unencrypted in memory. This only requires that the database is initialized with encryption and that the key used for initializing the database is accessible to the server during startup. A special configuration parameter provides the encryption key by specifying a custom key setup command for implementing special security requirements.
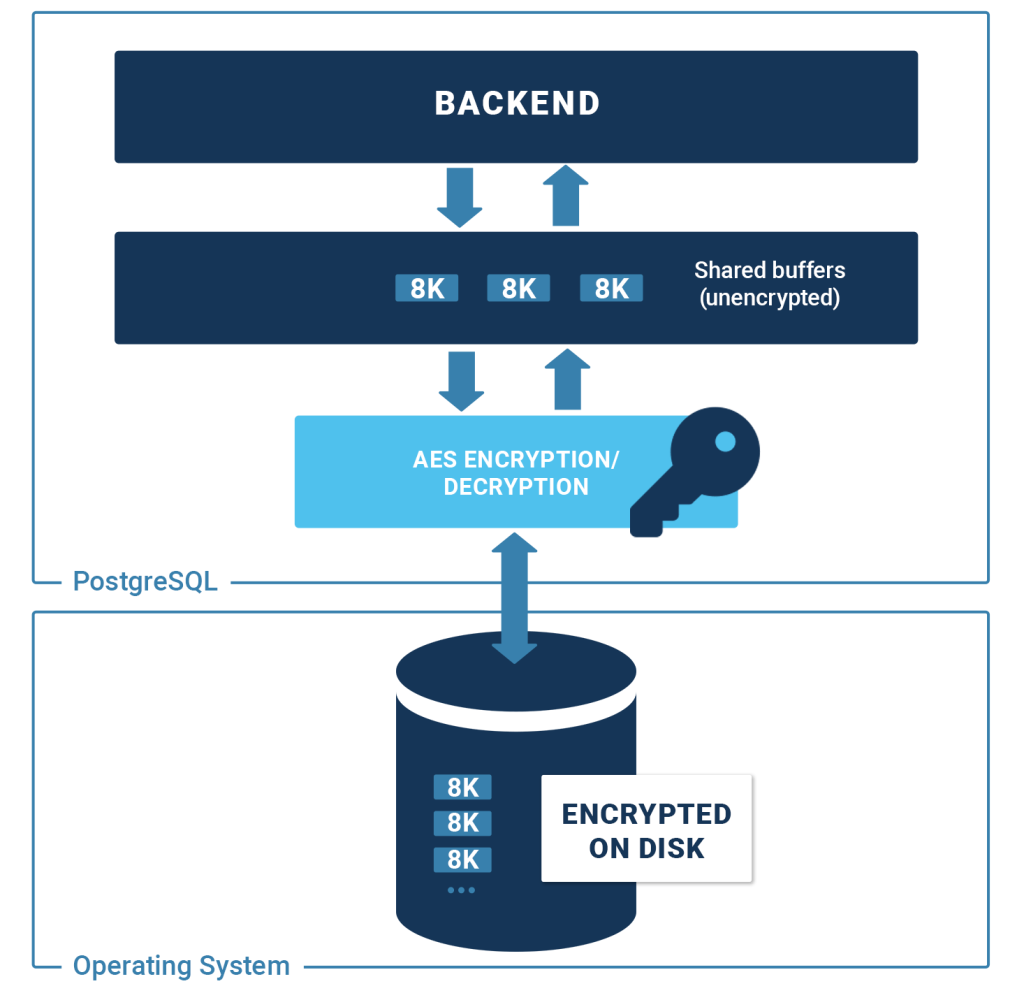
Since the data is stored on a disk, we naturally base our approach on “Disk Encryption Theory”. For each type of file, we use the AES cipher in the appropriate mode of operation. The AES cipher itself encrypts/decrypts individual blocks (encryption blocks) in the most efficient way possible. Your data will be safe on disk.
Fortunately, Intel and AMD offer superior hardware support for AES encryption. This ensures that PostgreSQL TDE has a minimal performance impact. We have seen systems encrypting and decrypting gigabytes of data per second on modern servers. Given a typical workload, the impact of TDE on performance is essentially negligible.
Security is not an isolated issue. To really secure a system, many layers must be considered and you must ensure that all components are covered. PostgreSQL TDE is therefore the ideal solution for your infrastructure.
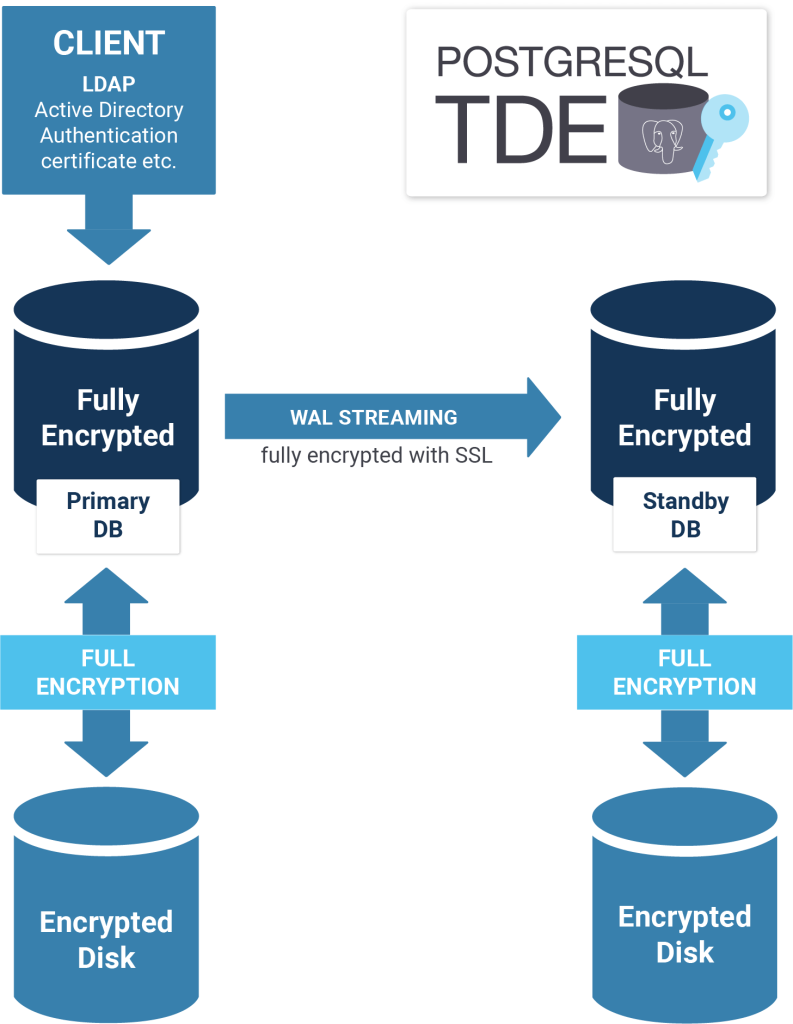
PostgreSQL TDE not only provides data-at-rest encryption, but also ensures encryption of the entire ecosystem including …
PostgreSQL TDE integrates perfectly into SELinux and provides a solid foundation for your entire infrastructure. In addition, it includes all functions of standard PostgreSQL.
Check out the performance analysis that compares PostgreSQL v13 with PostgreSQL Transparent Data Encryption: PostgreSQL Performance: encrypted vs. unencryped
Q: What does TDE actually encrypt?
A: Everything except pg_stat_statements extension data and transaction metadata.
Q: What is the encryption method?
A: Industry standard 128/192/256-bit AES-CTR cipher.
Q: Can I use another encryption method?
A: No, but we can build support for it.
Q: What performance penalty should I expect?
A: Hardware instructions accelerate encryption where available. TDE only applies encryption on I/O. Typical encryption and decryption speeds are 5GB/s per CPU core on modern hardware, higher than the I/O speed of the best available SSD devices. On normal workloads the overhead from encryption is not measurable.
Q: Can I upgrade to an encrypted database?
A: You will need to perform a dump and reload to an encrypted instance, or use logical replication to perform the migration online.
Q: Is it possible to encrypt only certain tables / tablespaces to win on performance?
A: Currently no. Since the transaction log needs to be fully encrypted in any case, and all changes normally go through there, it probably would not be a silver bullet to change that in the future.
Q: Is it possible to change the repl_proxy for cases when the repl_proxy gets compromised?
A: Currently, you should re-initialize a new cluster and dump / restore. However, you can use the key setup command to implement an encrypted key store and passphrase rotation for the master key.
Q: Does it integrate with my HSM?
A: Not at the moment. But if needed we can build support for it.
Q: I found a bug. Where should I report that bug to?
A: Please directly report any bugs or problems with TDE to bugs-tde@cybertec.at.